In part-1 we learned some terms associated with cybersecurity risks and threats. We also learned that threats and risks are inevitable – in life and business. One must anticipate and prepare for risks in advance. I also mentioned some cyber threats experienced by organizations. In this post I’d like to discuss some risk management strategies.
Image Credit: Image by Freepik
Monitoring
An event is an observable occurrence in a network or system. It could be a normal event like a routine process – or something unusual such as a large data outflow or someone accessing a database frequently. A CISO’s task is to respond to unusual events or behavior and take suitable actions to mitigate the risk. The network monitoring task is usually done by a team of security professionals in a security operations center or SOC – who use network monitoring tools to detect anomalies. The CISO should be on top of things and should respond with a plan or decision as soon as something unusual is detected (this is known as risk treatment).
Risk Identification
This is a recurring process for identifying different risks, classifying them, and then estimating the impact that each could have in disrupting the organization.
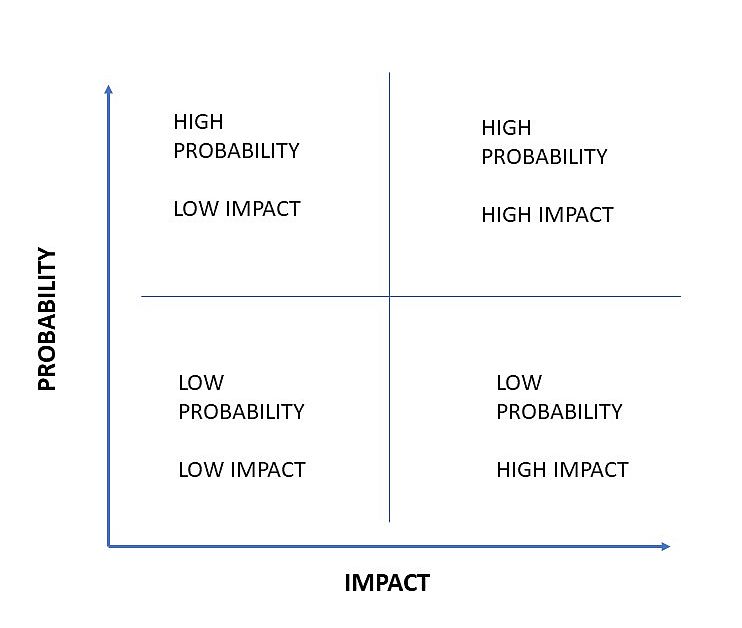
But how do you decide which risks are critical and which ones are not? This is where risk prioritization comes in. A risk matrix is an effective method to prioritize the risk.
When plotting the identified risk on a risk matrix, take a close look at your organization and analyze what makes it unique. What is its intellectual property? And will the risk impact that? In what way?
Security professionals must know their organization’s business domain. They must be aware about the strategic, tactical and operational plans.
Risk Assessment
Is a part of risk identification. Risk assessment is the process of identifying, estimating and prioritizing risks to an organization’s operations. That includes its mission, functions, image and reputation. You can even add the organization’s customers, employees, partners, and shareholders to that list. What would be the impact of the identified risk on all these entities?
Align each identified risk to an information system with the goals, objectives, assets or processes of an organization. This in turn aligns with or directly supports the organizations goals or objectives.
These days CISOs and CIOs are expected to be business enablers. Mapping risks to business goals is one of their business enablement tasks.
Once the risk assessment is completed it is documented and presented as a report to the management, who will then take a decision for risk treatment.
Risk Treatment
Risk treatment means determining the best course of action to respond to an identified risk. This decision is taken by the management who consider three key aspects:
- What is the management’s attitude towards risk and availability?
- The cost / time for risk mitigation
- Is the effort (in terms of resources, time and costs) that goes into mitigation worth it?
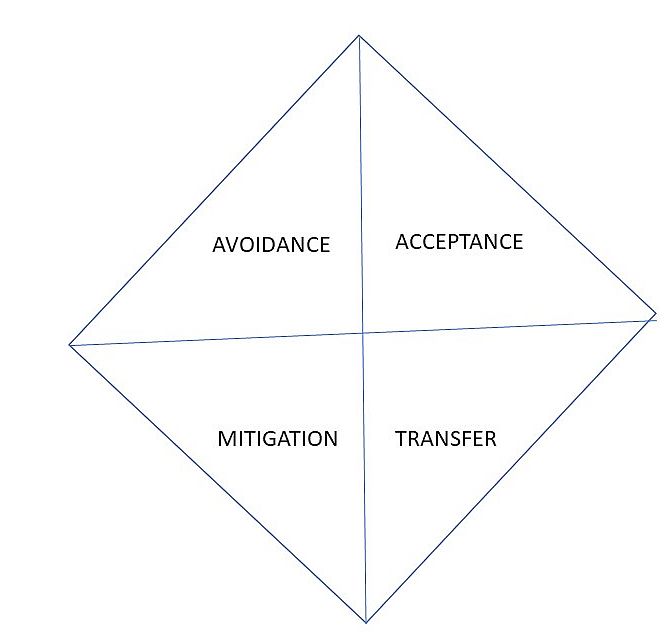
There are four paths to respond to the identified risk:
- Risk Avoidance
- Risk Acceptance
- Risk Mitigation
- Risk Transference
1. Risk Avoidance – Revisit the risk matrix. When the identified risk is placed in the second quadrant (High Probability, High Impact) the management may decide on risk avoidance. The potential impact of the risk is too high or the likelihood of the risk being realized is too great.
They may decide to shut down a website for maintenance or shut down a server that could be compromised. Of course, the key thing here is communication with all stakeholders that could be impacted by this action.
2. Risk Acceptance – When the impact or likelihood of occurrence is negligible then the management may choose to accept the risk. It’s like ignoring the risk. The benefit is more than enough to offset the risk.
In the risk matrix, this risk would be placed in the low impact quadrants.
3. Risk Mitigation – This is the most common type of risk decision taken. When the organization accepts the risk but takes actions to mitigate the impact on business operations.
Mitigation involves remediation measures and controls such as security controls, policies, procedures, standards to minimize the impact of the risk.
While risk cannot be completely eliminated, risk mitigation measures such as an incident response plan and safety procedures should always be established.
This type of risk would be placed in the high impact quadrants of the risk matrix.
4. Risk Transference – When the effort of dealing with the risk is too high and diverts resources from core business practices, one may choose to transfer the risk to a third party. This could be an insurance company or a special purpose vehicle – a company who will manage the risk in exchange for payment.
These days cyber insurance is becoming a common risk management strategy. However, the organization needs to set up a robust defense infrastructure that is fully compliant with industry frameworks and standards. The cyber insurer will need to determine that when it decides to accept the risk and set the premium amount.
Risk Management Tools
There are plenty of risk management and compliance tools to help you manage risks in a structured manner. Risk management consultants can also help you with compliance.
In closing, I advise all security professionals to get a good understanding of the business functions, goals and objectives. Identify the crown jewels to be protected and then use the risk matrix (and other risk management tools) to align the risk to the business goals and business assets.
Then take suitable risk decisions (risk treatment).
To comment on this post, write to the author at: [email protected]
Reference: (ISC)2 course material for the (ISC)2 CC course.
DIGITAL CREED is an initiative by technology journalist Brian Pereira